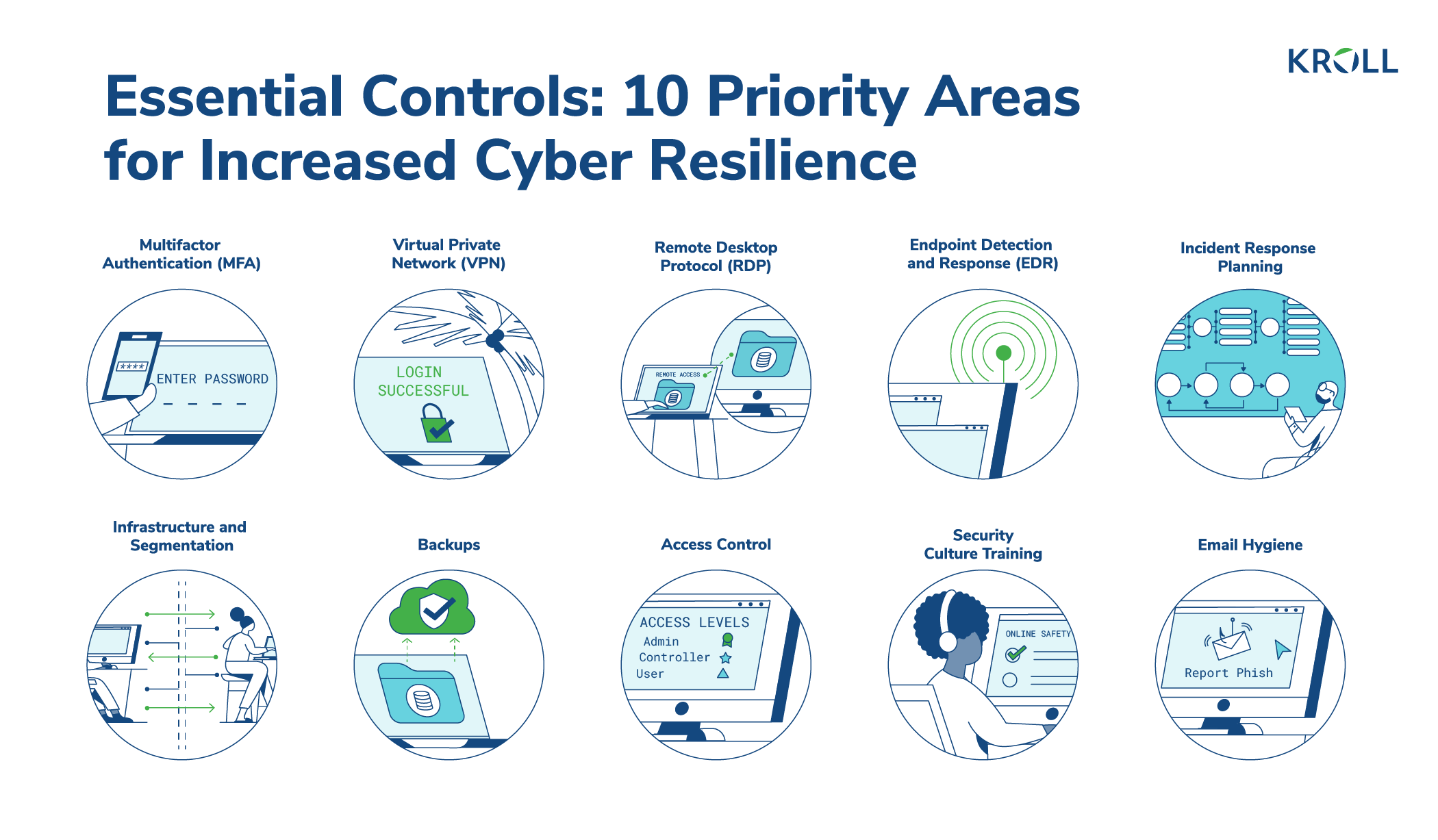
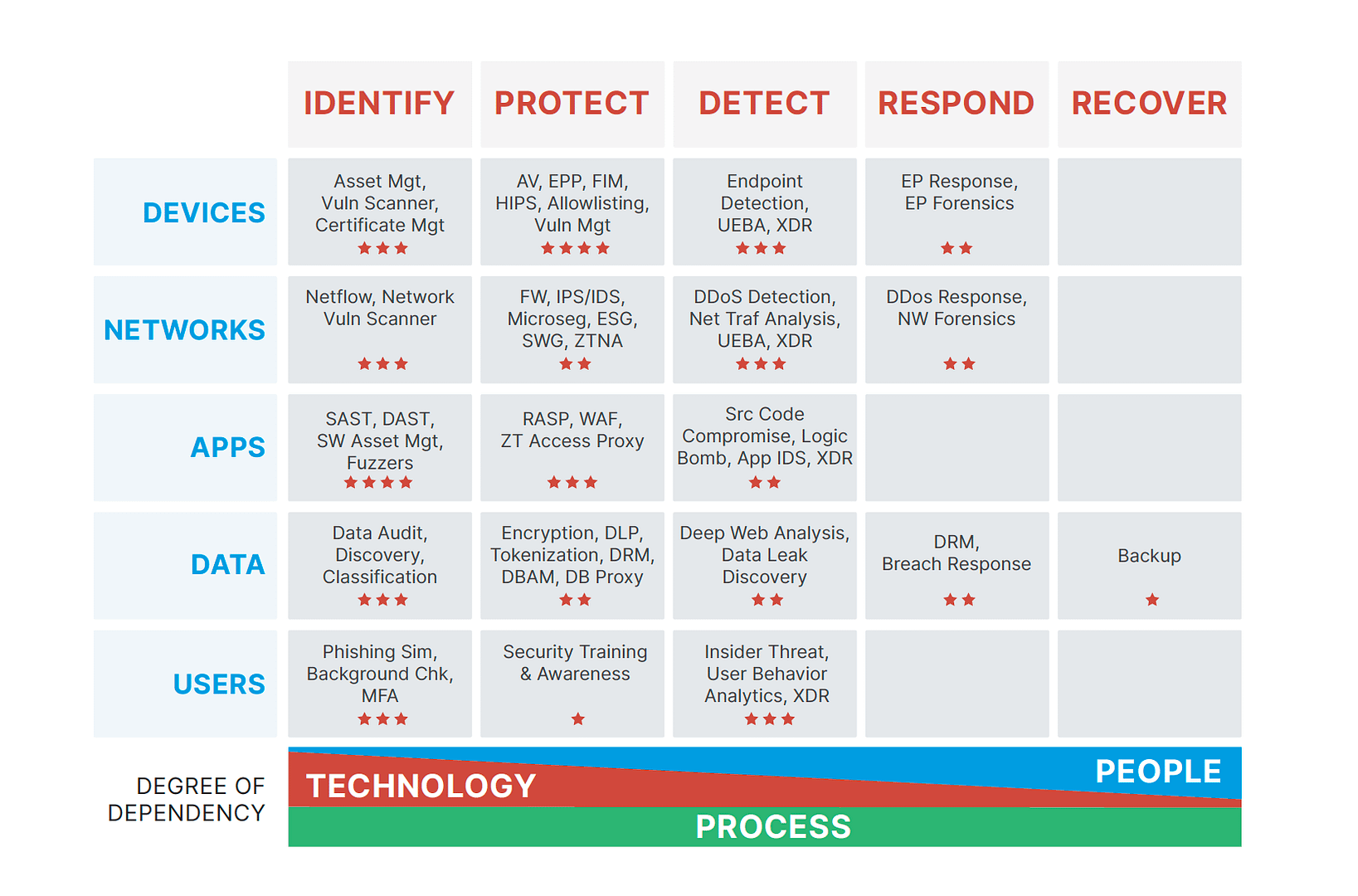
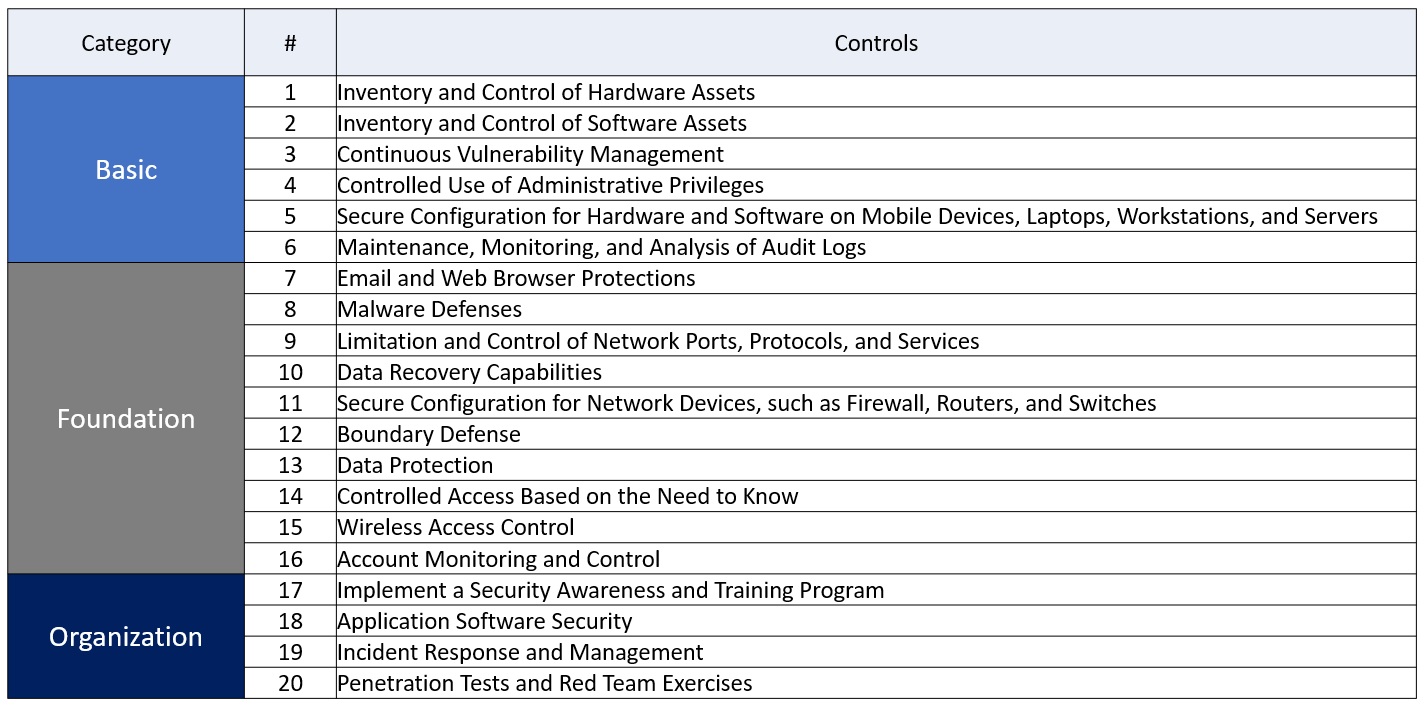
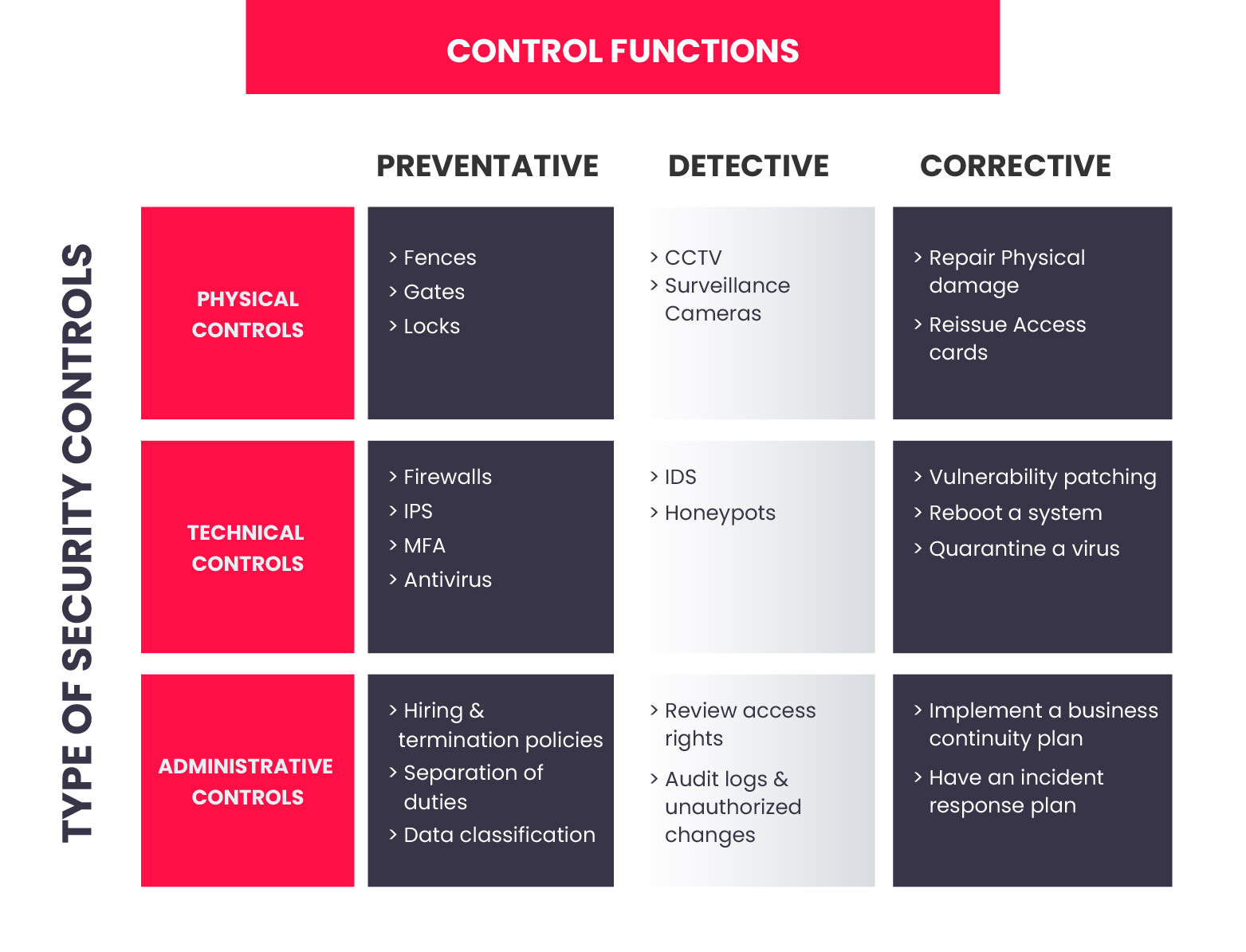
Top 10 IT security actions to protect Internet connected networks and information (ITSM.10.089) - Canadian Centre for Cyber Security
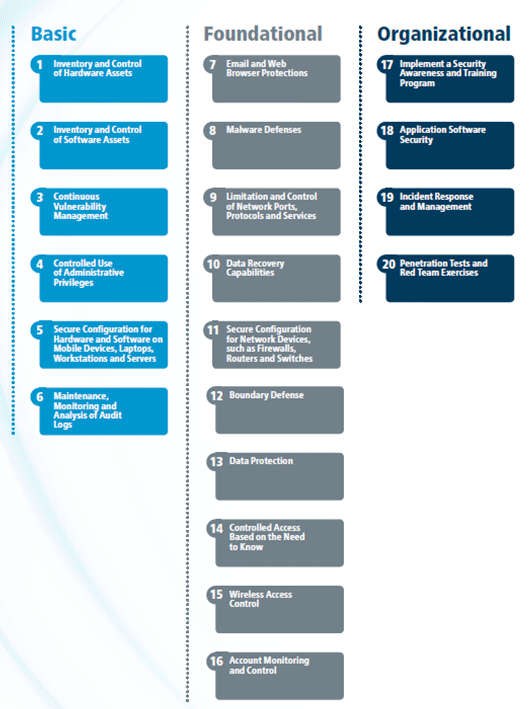
Transportation Management Center Information Technology Security - Chapter 3. Best Practices for Traffic Management Centers Information Technology Security - FHWA Office of Operations
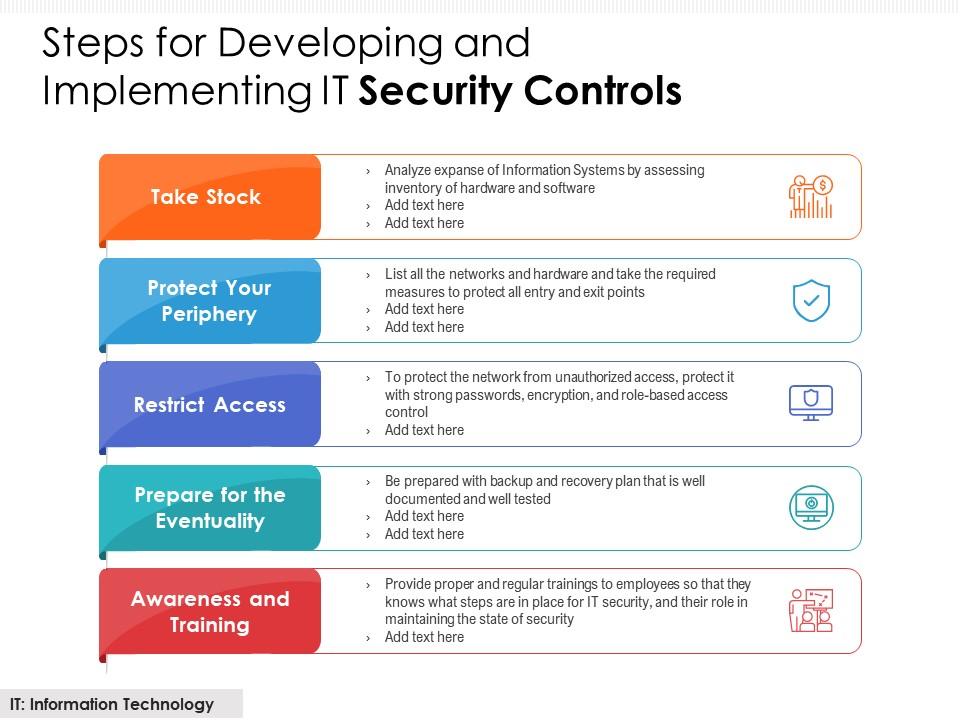
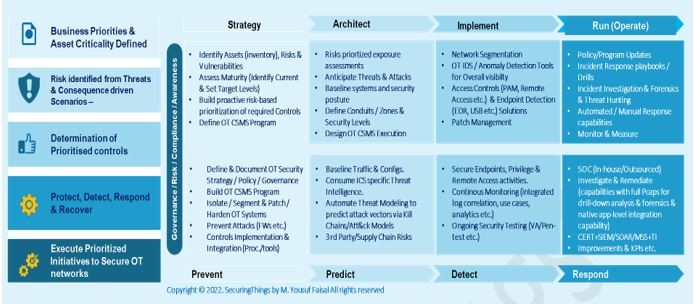
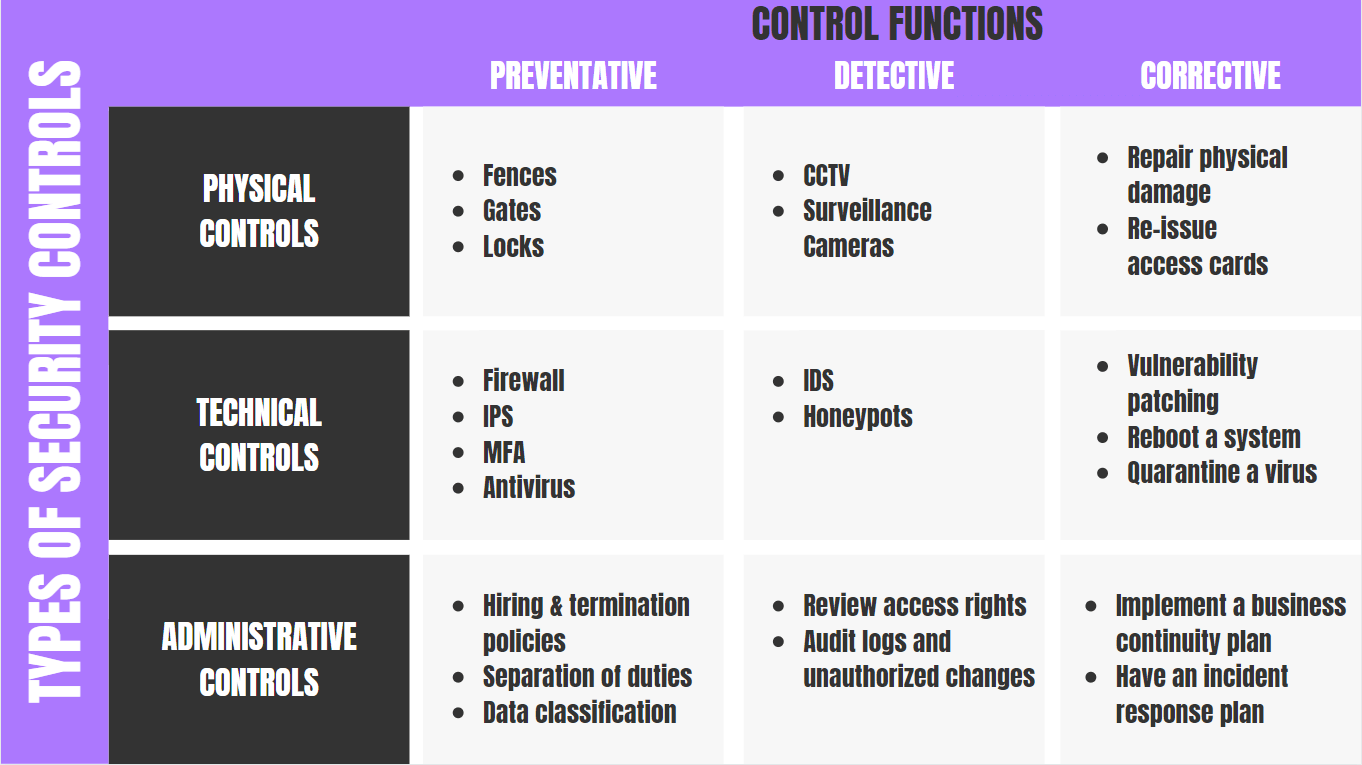
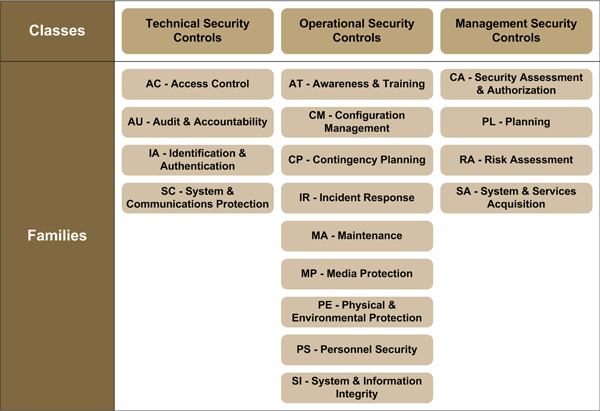
Steps For Developing And Implementing IT Security Controls | Presentation Graphics | Presentation PowerPoint Example | Slide Templates